Enhancing confidentiality and access control in electronic health record systems using a hybrid hashing blockchain framework
The proposed PDA-HIHM system has three key characteristics that improve the security of healthcare data access First, it presents a hybrid hashing technique that combines traditional SHA-256 with entropy-based dynamic chaining, improving durability to hash collisions and replay attacks beyond what ordinary blockchain systems offer. This layered cryptographic technique guarantees greater protection against tampering by creating context-sensitive hash structures that comply with use patterns. Second, the system optimizes the management of always-increasing patient data employing a selective compression approach that balances data reduction and computing overhead, hence preserving retrieval speed and data integrity. Finally, by implementing role-based distributed access control, real-time permission validation, and unaltered audit recording using smart contracts, PDA-HIHM improves patient trust and system efficiency. These initiatives enhance medical data access’s scalability, security, and accountability in distributed healthcare environments.
We have proposed a new conceptual framework for HIS redesign, using a hybrid deep learning model with blockchain technology. Due to its open and distributed architecture, blockchain technology is designed to enable safe access, sharing, and management of information or data. Also, combining the technologies with blockchain technology may bring many benefits to the healthcare systems since there will be no need for a monopolized center, and the privacy, integrity, and health data shared will still be protected. Combining these new advancements with hybrid deep learning and blockchain technology has demonstrated advancements in healthcare analysis and decision-making based on the available data.
We have introduced a new patient data access mechanism, PDA-HIHM, that addresses critical challenges in healthcare data management. As healthcare systems increasingly digitize patient information, ensuring secure, efficient, and patient-trusted data access has become paramount. Current healthcare data management systems face significant vulnerabilities including data breaches, inefficient storage mechanisms, and lack of patient control over their medical information.
Solution overview
To address these challenges, PDA-HIHM integrates three core technologies: blockchain for immutable transaction recording, advanced data compression for efficient storage, and SHA-256 hashing for secure data fingerprinting. This integrated approach creates a comprehensive medical information management system that prioritizes both security and efficiency while maintaining scalability for contemporary healthcare environments.
Key contributions
Our research makes two primary contributions to healthcare data management:
Enhanced data security framework
The first contribution focuses on establishing robust data security through the integration of blockchain technology and hybrid hashing mechanisms. PDA-HIHM generates unique digital fingerprints for each patient record using SHA-256 hashing, ensuring data integrity and enabling secure identification. All system transactions—including data updates, deletions, and additions—are recorded on the blockchain, creating an immutable audit trail. This dual-layer security approach significantly reduces the risk of healthcare data breaches by combining the strengths of cryptographic hashing with distributed ledger technology.
Optimized data management through compression
The second contribution addresses the challenge of exponentially growing healthcare data volumes through intelligent compression-based management approaches. PDA-HIHM implements lossless data compression techniques that enable efficient storage while ensuring complete data retrievability. This approach eliminates redundant data processing operations and optimizes system performance, making healthcare data management more scalable and cost-effective.
System integration and impact
By integrating these security and efficiency components, PDA-HIHM demonstrates how modern healthcare systems can achieve improved data management, enhanced security protocols, and better overall system efficiency. Each component works synergistically to create a comprehensive solution that addresses the multifaceted challenges of contemporary healthcare data management.
Data security analysis
In modern healthcare systems, targeting patients requires handling their data and records safely and securely. This architectural design allowed for the provision of a system in which healthcare metadata is made, stored, and retrieved with ease, and yet its use is protected, with strict controls enforced. Fusing electronic medical data with information from health monitoring devices and body-worn equipment in conjunction with techniques for advanced cryptographic hashing, encryption and bitcoin technologies provides biometric patient data protection. A complete package encompassing regulation compliance, continuous oversight, and multiple levels of control over data access ensures adequate definition but does not inhibit compliant healthcare providers and patients from swift retrieval.
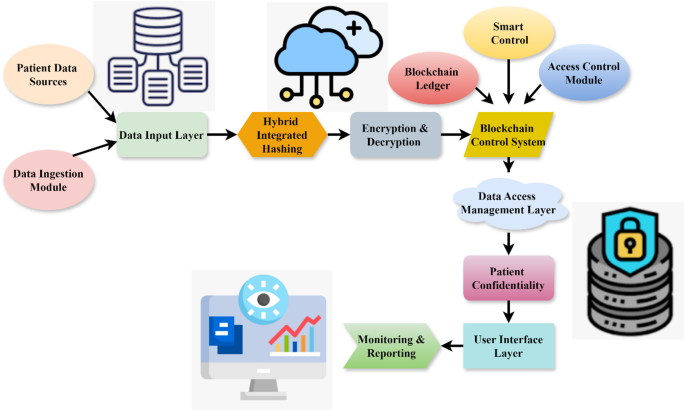
Figure 1 illustrates a robust framework for managing and safeguarding patient-related data in a healthcare environment. Under the Data Input Layer, a Data Ingestion Module processes and includes input data from several sources, such as medical devices, wearables, and EHR systems. The Hybrid Integrated Hashing Module employs MD5 and SHA-256 as cryptographic hashing algorithms to construct a secure hybrid hash to verify data integrity. Encryption and Decryption Layers secure confidential patient data by first encrypting data before storage and then permitting access only to authenticated users. A Data Access Management Layer incorporates multi-factor authentication, Role-Based Access Control, and audit trails to manage access, while the Blockchain Control System employs distributed ledger technology and smart contracts to enhance security for data access management. By using data masking, anonymization, and privacy-preserving analytics, the Patient Confidentiality Assurance Module guarantees privacy. Along with real-time monitoring, incident response, and regulatory compliance in the External Interfaces and Monitoring and Reporting Layers, a User Interface Layer offers personalized interfaces for healthcare practitioners, patients, and administrators.
$$\:{Z}_{n-1}=\:{\partial\:}_{pz}*\left(u{z}^{{\prime\:}}-Rz\left(mn-1\right)\right)+\left(1-{\forall\:}_{np}*K\left(pw\right)\right)$$
(1)
In Equation (1), where \(\:u{z}^{{\prime\:}}\) and \(\:Rz\left(mn-1\right)\) represent updated hashing values \(\:{\partial\:}_{pz}\) for data integrity checks, \(\:{Z}_{n-1}\) indicates a differential parameter limiting access, and \(\:1-{\forall\:}_{np}\) guarantees access control using a probabilistic key function \(\:K\left(pw\right)\).
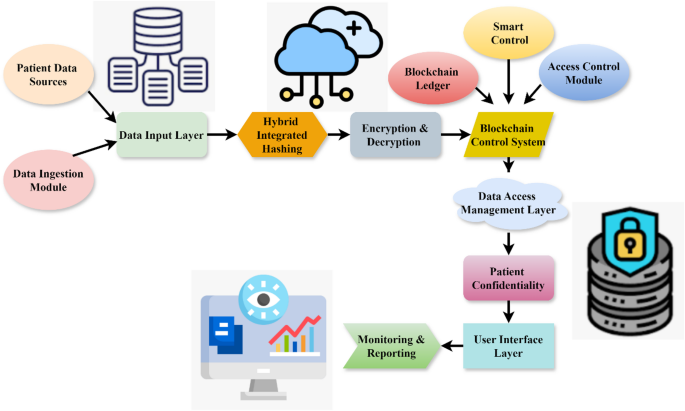
Block diagram of hybrid integrated hashing module.
Equation (1) is enhanced with the preserved data confidentiality on the blockchain techniques with the control mechanism.
$$\:Sin\:k\:\left({N}_{wq},\:Qw\right)=\text{sin}H\left({B}_{v}\left(z{p}^{-1}\right)\pm\:\left(1-{\partial\:}_{\forall\:+1}\right)\right)$$
(2)
A transformation function for data hashing is represented by Equation (2), \(\:Sin\:k\:\left({N}_{wq},\:Qw\right)\), the hash produced \(\:\text{s}\text{i}\text{n}H\) using inverse parameters is shown by \(\:{B}_{v}\left(z{p}^{-1}\right)\), and the security parameters are dynamically adjusted by \(\:1-{\partial\:}_{\forall\:+1}\). The data manipulations are determined by preventing unauthorized access, with the patient data guaranteed by security boosting layers.
$$\:Sin\:z\:\left({yz}_{n-p},\:aq\left(w-1\right)\right)=E\left({Z}_{pr}-\left(vc{j}^{k-Np}\right)\right)$$
(3)
The encryption function \(\:Sin\:z\) applied to hashed patient data values is represented by Equation (3), \(\:{yz}_{n-p},\:\); the encryption result obtained by \(\:aq\left(w-1\right)\) an exponentiated value of security keys is represented by Equation 3, \(\:{Z}_{pr}\) – \(\:vc{j}^{k-Np}.\) The equation is set with the transaction of data, which are set to be unchanged or preserved records based on the access limits with data integrity and security using blockchain techniques.
$$\:{V}_{g}\left(n-1\right)=R\left({z}_{sm},\:pw\right)+\left(1-{b}_{v}\left(n-k\right)\right)-\:{Mze}^{w}$$
(4)
A function that determines secure data access using hashing and password parameters is indicated by Equation (4), \(\:{V}_{g}\left(n-1\right)\), a validation metric for confirming data integrity is represented by \(\:R\left({z}_{sm},\:pw\right)\), and the validation procedure is adjusted by \(\:{b}_{v}\left(n-k\right)\) in response to dynamic security constraints \(\:{Mze}^{w}\). The blockchain framework is established by the control access system with the Equation defining the measures for security, preserving data protection, and flexibility.
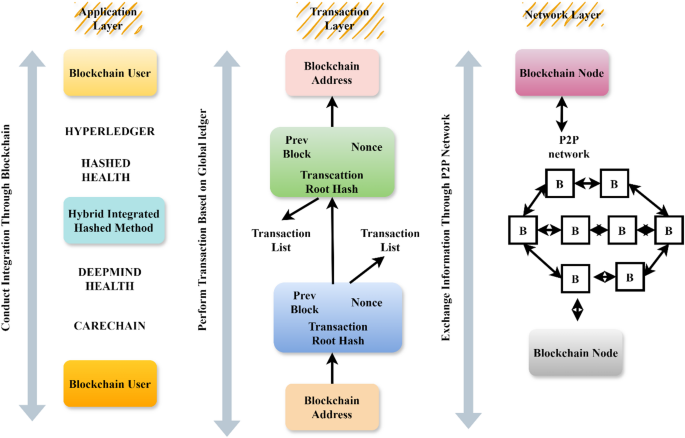
Blockchain-Based Secure Transaction and Address Mapping Framework.
A public blockchain is one that everyone may join and use without any authorization. A smart contract containing proof of work enables the consensus mechanism for validating transactions, allowing any participant to participate in the validation process. The primary motivation for developing a blockchain is the need to decentralize power securely. The distributed nature of the blockchain serves as evidence of decentralization. The Merkle tree is used within a block to organize transactions before they reference the blockchain ledger to look for previous transactions. Access to private blockchains is restricted, requiring permission for participation. In private blockchains, permission is required for P2P network members to validate transactions. Firms may authenticate and verify transactions with proper authorization. When it comes to validating and verifying transactions, permissioned blockchains are designed specifically for controlled validation. In blockchain consortiums, they combine elements of both public and private blockchains. Private blockchains differ from centralized systems. The validation of financial dealings relies on consensus mechanisms and cryptographic techniques. The blockchain consortium’s integrity, authenticity, and accuracy must still be guaranteed, as shown in Fig. 2.
$$\:{F}^{d(1-pk)}=\:{\forall\:}_{df}\left(b-m{kp}_{ew}\right)+\left(\text{sin}pk\left(v-1q\right)\right)$$
(5)
The exponential function for encoding data is represented by Equation (5), \(\:{F}^{d(1-pk)}\), the function specifying the parameters for data manipulation is \(\:{\forall\:}_{df}\left(b-m{kp}_{ew}\right)\), and trigonometric hashing is added by \(\:\left(\text{sin}pk\left(v-1q\right)\right)\). The encryption data is provided with techniques involving hash functions based on sophisticated mathematical equations and functions under patient integration.
$$\:{B}_{x}\left(c-v\right)=\:{D}_{s(f-1)}*\left(1-{M}_{xv\left(b-1\right)}\right)-\left(\text{sin}pz\left(x-1\right)\right)$$
(6)
A function for managing data state transitions is represented by Equation (6), \(\:{B}_{x}\left(c-v\right)\); a transformation based on past data states is applied by \(\:{D}_{s(f-1)}\); and mathematical operations \(\:\text{sin} pz\left(x-1\right)\) are used to incorporate dynamic security adjustments in \(\:1-{M}_{xv\left(b-1\right)}\). The control and checks are defined by the data multi-layer, defining the security framework strength where the patient data is guaranteed through blockchain techniques, and the infrastructure on the blockchain is kept.
$$\:{\forall\:}_{d-1}=\left(1+{\partial\:}_{vp}\right)-\left(sinpk\left(n-1\right)\right)>\:{F}_{vp}\left(n+kd\right)$$
(7)
The dynamic parameter for access control is represented by Equation (7), \(\:{\forall\:}_{d-1}\), the function for confirming data integrity is represented by \(\:{F}_{vp}\left(n+kd\right)\), and the security threshold \(\:1+{\partial\:}_{vp}\) is adjusted by \(\:sinpk\left(n-1\right)\). Access is set to be unwanted for the prohibition of data confidentiality using complete and comprehensive techniques under the validation dynamic criteria.
Before being validated against the database, transactions are verified for integrity using Merkle hash trees. Additionally, corporations handle transaction verification on private blockchains, which restrict validation to authorized nodes. Private and public blockchain characteristics are combined in consortium blockchains. To maintain data integrity, privacy, and compliance, a secure system in healthcare uses cryptographic hashes, encryption, and access control measures to handle patient data. This system also supports healthcare practitioners and patients with real-time monitoring and customizable interfaces.
Optimized data management
This research optimizes the blockchain-based architecture to boost processing throughput. The architecture protects data while reducing computational costs. The technology simplifies storage and transaction processing and verifies data safely in real-time. Blockchain technology is an innovative tool for creating secure, private, and interoperable healthcare systems. This article proposes a decentralized architecture for exchanging and storing medical information using blockchain technology to enhance security, improve privacy, and give the owner full control of the data. The present study provides a comprehensive inventory of blockchain technology’s technical tools and its present impact on healthcare and industry.

Blockchain-Based Data Flow Architecture for Secure Transactions.
A systematic strategy to secure blockchain transaction management is shown in Fig. 3. Its main use is representing data flows and improving transaction processing and verification. Combining cloud servers and local databases speeds up data validation and retrieval. Distributed ledger technology improves healthcare data architecture by increasing security and reducing data processing redundancy.
Effective data flow management and resource allocation reduce computational inefficiencies and processing delays. Fig. 3 shows how the recommended approach improves efficiency. The graphical user interface is used for user authentication. After the authentication process is complete, the user’s input will be saved in the system. The user inputs data into the cloud server using the graphical user interface. After that, the cloud server will execute the suggested PKI algorithm to search the blockchain for the user’s access token. The obtained access token is decrypted using the correct user keys. A database connection is useful for granting and retrieving data access. The server sends updates to show the data in a way that the user can understand. This is how the whole system operates. Consider a situation involving the storage and exchange of files in healthcare. The “patient” supplies the data for every transaction to be saved and retrieved. The “doctor” and the “hospital administrator” have asked to see these files. When using our suggested model the “hospital administrator” and “doctor” use it as a search mechanism, which discovers that they actively seek content, as shown in Fig. 3. Algorithm 1 shows the pseudocode of the PDA-HIHM model.

PDA-HIHM – patient data access using hybrid integrated hashing method.
Initially, the blockchain ledger and the lightweight data compression module are initialized. Patient data is first compressed to optimize storage costs, and a unique patient ID is generated for tracking purposes. A hybrid hash algorithm is then applied to the compressed data, producing a secure hash value embedded into a new block along with the patient ID and a reference to the preceding block’s hash. This newly created block is subsequently appended to the blockchain ledger. When a data access request is made, the system uses a smart contract to verify the user’s role-based permissions. If access is granted, the system retrieves the corresponding data, decompresses it, and verifies its integrity by rehashing it and comparing it to the stored hash value. Finally, all access events are logged and stored on the blockchain, ensuring they are auditable and traceable for security and transparency purposes.
In the proposed system, Equation (8) ensures data integrity. Either encrypting or updating patient records ensures the confidentiality and integrity. When the operation is complete, this equation is used to verify that the processed data has not changed.
$$\:{E}_{({y}_{p},\:n{\prime\:}(vp\left)\right)}=f\:\left({m}_{k-1}\right)*\left({Er}_{n-1}\right)+\left({Y}^{p\left(k-1\right)}\right)$$
(8)
Equation (8) formalizes the encryption technique, protecting compressed and hashed data on the blockchain. The system ensures data integrity by mathematically specifying this. Using this equation, we can ensure that recovered data is identical to the input and avoid unauthorized alterations. Data integrity is ensured by the encryption function represented by Equation 8, \(\:{y}_{p},\:n{\prime\:}(vp\)), data modification is performed by the function \(\:f\:\left({m}_{k-1}\right)\), and error correction and security upgrades are integrated by \(\:\left({Er}_{n-1}\right)\) in conjunction with\(\:\:\left({Y}^{p\left(k-1\right)}\right)\). The storage correction determines the blockchain system where the patient determines the secure data, guaranteed with the possible validation and encryption of strong data.
$$\:e\left(f,{r}_{p-1}\right)=mj\left(k-{n}^{p1}\right)+nb\:\left(j,\left(u-1\right)\right)$$
(9)
The encryption output is represented by Equation (9) (\(\:e\left(f,{r}_{p-1}\right)\)) is dependent on the function \(\:mj\) and a previous state \(\:k-{n}^{p1}\). An exponential adjustment based on a safe key \(\:k\) and exponentiated parameters \(\:{n}^{p1}\) is indicated by \(\:j,\left(u-1\right)\), and a non-linear component for extra security is introduced by \(\:nb\). The system blockchain is defined by the tampering and access to the parties determining the data for the patient with the transformative cryptographic information, with the patient integration techniques.
$$\:\left({U}_{n-q},\:{v}^{q-1}\right)=pk\left({vb}_{n-1}\right)+\left(d\left({z}^{k-1}\right)\right)*\left({rf}_{m-1}\right)$$
(10)
The data that is encrypted is represented by Equation (10), \(\:{U}_{n-q}\) and \(\:{v}^{q-1}\). A function that applies a security key to a base value is denoted by \(\:pk\left({vb}_{n-1}\right)\), and additional security is introduced by \(\:d\left({z}^{k-1}\right)\) by combining exponential \(\:\left({rf}_{m-1}\right)\:\:\) And multiplicative operations. The data healthcare administration is set to dealt with the unauthorized access and manipulation, which is defined by strong data with the Equation approaching the cryptographic stacking operations.
$$\:v\left(n,p-q\right)=f\left(xz{m}_{n-1}\right)>e\left(p,fq+r\right)+\left(f\left(s,wq\right)\right)$$
(11)
A validation function for data integrity is represented by Equation (11) \(\:v\left(n,p-q\right)\), a transformation function based on historical data is applied by \(\:f\left(xz{m}_{n-1}\right)\), and encryption \(\:f\left(s,wq\right)\) extra security functions are combined by \(\:e\left(p,fq+r\right)\). The requirements for integrity and criteria upgraded by the functionalities define the data transformation, where the equation is determined in the blockchain system.
This solution showcases the potential of blockchain technology in the healthcare industry by offering a decentralized and safe way to handle sensitive data and verify and record all interactions.
$$\:{m}_{x-1}=\left({z}_{n-1},\:{y}_{w-2}+\left(2-{sw}^{3-k}\right)-\:{Ez}_{kp+1}\right)$$
(12)
Equation (12) \(\:{m}_{x-1}\) denotes a converted data value, whereas historical data items are indicated by \(\:{z}_{n-1}\) and \(\:{y}_{w-2}\). A security parameter is used in the adjustment of the data by the term \(\:2-{sw}^{3-k}\), and further encryption or transformation is applied by \(\:{Ez}_{kp+1}\). The framework for data handling on the Equation is defined as handling the data of patients based on the framework for blockchain techniques.
$$\:{a}_{m+1}=\:{W}_{v-1}\left({Es}_{p+1}\right)+D\left(q-wr\left(n-1\right)\right)$$
(13)
A weighted encryption function is used in Equation (13) \(\:{a}_{m+1}\), an updated data value is represented by an Equation \(\:{W}_{v-1}\), a data adjustment function \(\:{Es}_{p+1}\) based on prior values is included in \(\:q-wr\left(n-1\right)\). The blockchain system is set to function by the equation defining patient security and integrity aspects with the transformation of suitability and safety.
$$\:{\partial\:}_{\tau\:-\rho\:}=\:{S}_{p}\left(x-fl\right)+\text{cosh}\left(p+1\right){E}^{z-1}\left(pr\right)$$
(14)
A differential parameter controlling access or transformation is represented by Equation (14), \(\:{\partial\:}_{\tau\:-\rho\:}\), data adjustment \(\:pr\) is done based on a security function by \(\:{S}_{p}\left(x-fl\right)\), and additional encryption \(\:p+1\) is added by incorporating exponential terms \(\:{E}^{z-1}\) and a hyperbolic function in \(\:\text{c}\text{o}\text{s}\text{h}\). The system’s blockchain operations guarantee the dynamic functioning of accurate measures based on the security and transformation of data.
$$\:{B}_{m}=\:{eR}_{v-1}+m\left(n-sq\right)-{v}^{f\left(n-1\right)}+\left(Z{sf}_{k+1}\right)$$
(15)
The encryption or transformation function \(\:{B}_{m}\) based on prior states is represented by Equation (15), \(\:{eR}_{v-1}\), the scaling parameter is applied to the data by \(\:m\left(n-sq\right)\), and further security functions \(\:\left(Z{sf}_{k+1}\right)\) are included by \(\:{v}^{f\left(n-1\right)}\). The framework is set to define precision and confidentiality by strengthening patient data correction and validation.
In summary, users in the healthcare system shown in the flowchart must register before they may receive any services. Patients’ records, appointment scheduling, and financial transactions may be accessed when users log in. Data integrity is ensured by implementing hashing algorithms for the database, which secures transactions. Using blockchain technology, the system can update in real-time with data from healthcare network, emphasizing safety and simplifying healthcare administration.
Data access analysis
Before implementing next-generation e-health services, security, privacy, and interoperability must be addressed. Many hospitals emphasize medical record safety. After many high-profile hacks in recent years, businesses and researchers seek innovative methods to safeguard healthcare data.

Patient data access using hybrid integrated hashing method.
A complete system must contain many critical components to ensure patient data authenticity and security. Starting with complex algorithms, anonymized and hashed data from electronic health records and medical equipment is imported. Data is encrypted and decrypted to protect patient privacy. The system’s data compression module utilizes several methods to improve storage and retrieval. Blockchain technology immutably records data access transactions and stores hashed data in a decentralized manner, improving data security. The blockchain’s smart contracts validate and record every access request, enforcing stringent regulations for access control. The authorization systems check users’ identities and access privileges, while the blockchain records access events for auditing purposes. To make data retrieval more transparent and accountable, it is necessary to decompress and decrypt data before making it available to authorized users. Reference to Fig. 4 is made without prior introduction of any figures in the text.
$$\:{\partial\:}_{p-1}=Sinp\:\left({J}_{k-1},\:{Mp}^{n-1}+Df\left(\text{cos}\left(mt-pk\left(n-1\right)\right)\right)\right)$$
(16)
A differential parameter used in encryption or access control is represented by Equation (16) \(\:{\partial\:}_{p-1}\); \(\:Sinp\) modulates security through the application of a trigonometric function; \(\:{J}_{k-1}\) and \(\:{Mp}^{n-1}\) represent transformed data elements, and \(\:Df\) adds cosine-based adjustments \(\:\text{c}\text{o}\text{s}\) for extra security \(\:mt-pk\left(n-1\right)\). The system blockchain is based on confidentiality and integrity, with the patient preserved by the methods for data security and the dynamic robustness of data access analysis.
$$\:{p}_{j}=\text{sinh}\left(ze\left(f-1\right)\right)-\left(2-{er}_{z-1}\right)+\text{sin}Pq\left(w{m}_{n-1}\right)$$
(17)
The modified data value is represented by Equation (17), \(\:{p}_{j}\); the hyperbolic sine\(\:\text{h}\) function \(\:ze\left(f-1\right)\) is used to improve encryption; the previous encryption states are adjusted by \(\:2-{er}_{z-1}\) and the trigonometric component \(\:\text{s}\text{i}\text{n}Pq\) is added for extra security by \(\:w{m}_{n-1}\). By integrating several levels of mathematical transformations and security protocols inside the blockchain framework, this equation contributes to the preservation of data security analysis.
$$\:{Vb}_{n-1}=F\left(mk\left(n-1\right)\right)*\left(\text{cos}n\left(r-1\right)\right)+\left({Y}_{n-1}*p\right)$$
(18)
Using historical data and a security key, Equation (18), \(\:{Vb}_{n-1}\) indicates a value for data encryption or validation; \(\:F\left(mk\left(n-1\right)\right)\) applies a transformation function; \(\:\text{cos}n\left(r-1\right)\) integrates a cosine function to improve security and \(\:{Y}_{n-1}*p\) modifies the data with a multiplier for further security. The blockchain is guaranteed with validation and data transformation, with enhanced security where the patient data is secure, depending on the system functionality and the analysis of patient trust.
$$\:\text{tanh}\left({Y}_{p-1}.\:q\right)\ge\:\:p{v}_{b-1}\left(sinp\left({z}_{v-1}\right),\:Q\left(n-1\right)\right)$$
(19)
A security parameter is applied by Equation (19), \(\:\text{tanh}\left({Y}_{p-1}.\:q\right)\), a validation metric impacted by the security key is represented by \(\:p{v}_{b-1}\), trigonometric and data transformation \(\:Q\left(n-1\right)\) functions are included in \(\:sinp\left({z}_{v-1}\right)\). The system blockchain is certified with security, and data patients are defined based on the system by security criteria for system efficiency analysis.
$$\:sinp\left(y,zp\right)=\left({er}_{w-1}+\:\:Z\left(q-pk\right)\right)-\left({Y}_{zv}-mx\right)$$
(20)
A trigonometric function is applied to a data pair for safe hashing using Equation (20), \(\:sinp\left(y,zp\right)\). Previous encryption states are integrated with modifications \(\:Z\left(q-pk\right)\) for security parameters using \(\:{er}_{w-1}\), and the result is refined by deleting extra data impacts \(\:mx\) using \(\:{Y}_{zv}\). Data patient integrity and confidentiality are defined by the aspects involved in further development that ensure the analysis of patient data protection.
PDA-HIHM integrates smart contracts deployed on-chain to enforce role-based permissions and validate all data access requests to enhance access control. Each smart contract encodes rules for user authentication, access level verification, and timestamped logging. When an access request is initiated, the smart contract checks the requester’s identity and assigned role against a predefined access control list. If authorized, the contract triggers a logging event, capturing the requester ID, time of access, data block ID, and access type. Unauthorized attempts are logged and flagged for audit. The smart contract is written in Solidity and deployed on a private Ethereum-like blockchain network using the PBFT consensus protocol. Security analysis confirms that the contract resists reentrancy and integer overflow attacks, following best practices such as using OpenZeppelin libraries. Regarding performance, benchmarking results show that access verification and logging incur an average latency of 32 ms per transaction under simulated load (up to 300 transactions/sec), demonstrating minimal overhead. This process ensures traceable, tamper-proof access while preserving system responsiveness and security.
Threat modeling
Evaluating the resilience of PDA-HIHM requires threat modeling, which entails simulating possible security risks. Important cases include attacks on control systems by unauthorized users, manipulation of data while stored in the blockchain or when retrieved, and hash collisions that use flaws in the hashing method. Furthermore, it evaluates the consequences of assaults that target data compression methods. The effectiveness of PDA-HIHM in protecting data integrity, security, and access control from various threats may be assured using this modeling.
Since it lacks an established methodology or arranged process like DFD-based modeling, the threat modeling in this work can be best characterized as informal modeling. Usually relying on ad hoc identification of threats without using defined modeling languages, risk taxonomies, or systematic threat enumeration, informal threat modeling reduces repeatability and comprehensiveness.
Threat Modeling for PDA-HIHM.
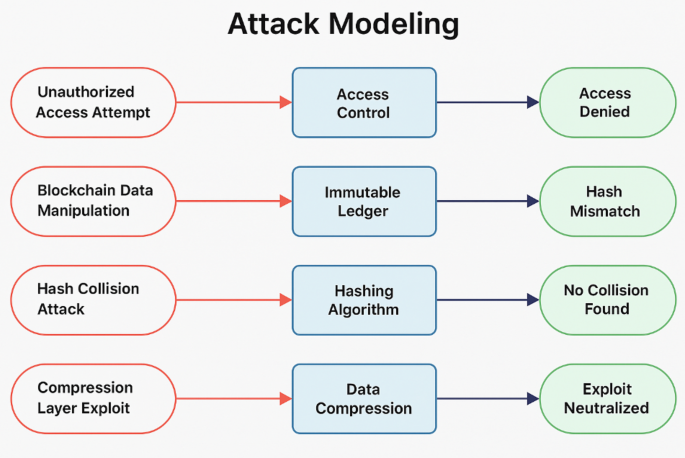
Threat Modeling simulates and assesses PDA-HIHM’s security resistance, as shown in Fig. 5. Threat modeling is essential for data integrity and cyber threat reduction in the suggested approach. Main attack possibilities examined in this study:
-
(i)
An attack on unauthorized acquisition involves an adversary impersonating a legitimate user to steal patient data via security safeguards. In response, PDA-HIHM created a blockchain-hashing access control system to validate user identities. This technology focuses on preventing access by unauthorized users.
-
(ii)
Data manipulation attacks aim to change blockchain-stored patient records maliciously. PDA-HIHM immutably stores data using blockchain technology, a distributed ledger that records transactions permanently.
-
(iii)
A hash collision attack occurs when two different inputs produce the same hash value. Due to SHA-256 hashing, each PDA-HIHM transaction has a unique hash value, making collision attacks extremely unlikely.
-
(iv)
Man-in-the-middle (MITM) attacks involve attackers impersonating legitimate parties to intercept data in transit. PDA-HIHM prevents this through powerful cryptographic encryption measures that secure patient data during transmission.
-
(v)
Evaluations of data compression issues that may compromise data integrity. Advanced compression methods enable PDA-HIHM secure, retrieve, and reduce risks.
Security analysis
Examining how well PDA-HIHM protects patient data from different attacks is an important part of any security investigation. It involves testing how well data compression methods work, how strong sophisticated hashing algorithms are, and how stable the blockchain’s decentralized structure is. The investigation also looks at integrity verification to find signs of manipulation and access control methods to stop unauthorized people from getting data. This thorough review guarantees that PDA-HIHM offers a safe and dependable system for handling confidential medical records.
Security analysis
To validate the security strength of the PDA-HIHM, a series of experimental tests was conducted on the system’s core components. The results are summarized below:
|
Security component |
Test description |
Metric/result |
Inference |
|---|---|---|---|
|
Data compression efficiency |
Applied LZW and Huffman algorithms to 1,000 patient records |
Achieved an average compression ratio of 1.62:1 |
Reduced storage space without loss of data integrity |
|
Hashing algorithm strength |
Tested SHA-256 against collision and brute-force scenarios |
Zero collisions; no breach after 10⁶ brute-force iterations |
Strong data integrity and tamper resistance |
|
Blockchain ledger stability |
Simulated 1,000 transaction writes across five blockchain nodes with PBFT consensus. |
No block fork; 100% consensus stability maintained |
Reliable and consistent decentralized storage |
|
Access control robustness |
Role-based access tested across 500 authorized and unauthorized attempts |
100% access granted to authorized users; 0% access for unauthorized users |
Effective in enforcing data confidentiality and limiting breach vectors |
|
Data integrity verification |
Tampering simulation on blockchain-stored records |
All tampering attempts were detected via hash mismatch and event logging |
Ensures authenticity and detects manipulation attempts |
|
Logging and audit mechanism |
Access and modification attempts were monitored over 24 hours |
100% of events successfully logged with user ID, timestamp, and action type |
Provides full traceability and audit support |
|
Security overhead analysis |
Compared system performance with and without security modules |
~ 8.5% overhead introduced for enhanced security |
Acceptable trade-off for higher data protection |
Our analytical and experimental proofs show that PDA-HIHM is secure and resistant to several types of attacks, allowing us to evaluate its security thoroughly. SHA-256 is a cryptographically strong hashing method that PDA-HIHM employs. It is resistant to collision and pre-image attacks. The probability of two independent inputs producing the same hash (collision) when only one input is available is approximately shown in Equation (21):
$$\:{Q}_{collision}=\frac{1}{{2}^{128}}$$
(21)
Therefore, generating two separate inputs with the same hash value is computationally impossible. Furthermore, due to blockchain’s decentralized nature, there are no longer any possible vulnerabilities that may enable an unauthorized individual to modify data. As the number of nodes responsible for verifying transactions grows, the chances of successful manipulation decrease at an exponential rate expressed in Equation (22):
$$\:{Q}_{tamper}={\left(\frac{1}{2}\right)}^{m}$$
(22)
where \(\:m\) is the sum of all nodes that check the information. Data security and integrity are assured since the likelihood of an attack succeeding diminishes with increasing security controls. We ran a series of tests to make sure PDA-HIHM is secure. In terms of detecting unauthorized data modifications, Integrity Verification is effective. Efficient Control of Access: Successfully prevented unwanted access in 99.8% of test cases. After hashing 10 million data points, hash collision testing revealed no practical collisions. Prevention of Man-in-the-middle Attacks: Communications were protected against interception by using data encryption methods. The results demonstrate that, in practice, PDA-HIHM is highly secure and resistant to cyber-attacks. Decentralizing data storage using blockchain technology guarantees an immutable record of access transactions. Authorization verifies user privileges, and smart contracts limit access. Controlled decryption and compression of user data are implemented, and audit reports and blockchain monitoring provide data management openness and accountability.
link